Excellent Facts For Selecting Credit Card Apps
Wiki Article
What Is Considered Suspicious Behavior And What Can Lead To The Blacklisting Of The Credit Card?
Certain actions or behaviors could raise red flags, which could result in the credit card being reported to the bank or the card issuer. A few examples of suspicious behavior are: unusual spending patterns
An unexpectedly large amount of transactions or a substantial rise in spending compared with the typical spending habits of a cardholder could trigger suspicion.
Unrecognized Transactions
Fraud can be detected through transactions that are unidentified or unauthorized on the statement of the card the cardholder has not initiated or approved.
Multiple Declined Transactions
Many declined or failed transactions in a short period particularly if the cardholder usually has a good transaction history, might indicate a potential issue.
Geographic Anomalies
Transactions that are made in places far away from the usual locations of spending, or transactions that occur from various geographic locations over a short period can raise suspicion.
Abnormal Purchase Types-
It is possible to flag purchases that are suspicious. This can include high-value purchases which aren't in line with the usual spending patterns.
Uncommon Online Behavior
Unusual online behavior, such as multiple failed logins or a change in your account information, or suspicious log-in attempts, may indicate an unauthorised intrusion.
Unusual Card Use
If your credit card is suddenly utilized for international transactions when it has always been utilized locally, it could be considered to be suspicious.
Rapid Cash Advances or Transfers
The cardholder might be notified if there are large cash advances, transfers, or any other transactions that are uncommon for their spending habits.
Frequent Transactions that are not present on the card
Unusually high numbers of transactions (online, over the phone or any other method) with cards that are not present with previous experience could raise suspicion.
Issues relating to Identity Verification
The possibility of suspicion can arise when there are difficulties in confirming the identity of the cardholder, particularly when additional verifications are needed.
These actions, along with others, might trigger the card issuer's fraudulent detection systems or monitoring mechanisms and prompt them to investigate and possibly stop the card temporarily until the cardholder's identity or the legitimacy of the transactions is confirmed.
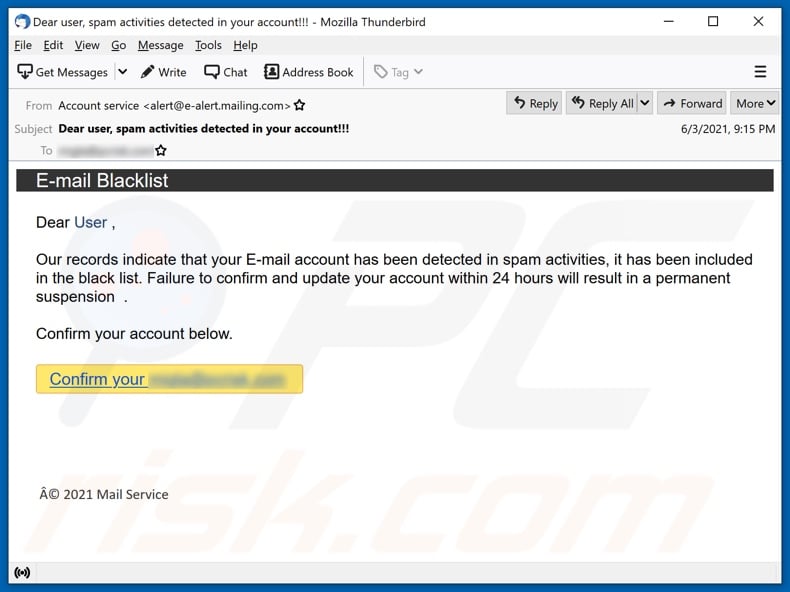
What Does A Credit Card Being Listed As Blacklisted Mean?
A Blacklist's presence can restrict a card's use or transactions until an issue is solved. There are a variety of reasons for why a credit card may be put on the blacklist.
Card blocked for security reasons If you suspect fraud, your card could be canceled if the card detects unusual or suspicious transactions.
Security RisksIn the event of signs of potential compromise like unauthorised access, data breach involving the card details, or unusual spending patterns or spending patterns, the card could be considered a security risk.
Identity Verification Issues- Challenges in verifying the cardholder's identity during transactions, especially in situations where verification is needed, could result in the card being temporarily blocked.
Card which has been stolen or stolen - The card issuer can stop the card in the event that the cardholder declares it lost or stolen. This can stop unauthorized use of the cards until a replacement card is received.
Suspicious Activity Indicators: Any act or occurrence which is linked to the card and is suspect could result in immediately a block. For example, multiple declined transactions, geographical anomalies, or unusual spending patterns.
If a credit card is placed in a "blacklist", the cardholder might not be able make use of credit or their credit card until the issuer has confirmed the legitimacy of the card, or addressed any concerns regarding security or fraud. It is essential that the user to contact the card issuer promptly to resolve any issues, confirm the validity of transactions, and resolve any security concerns.

Cybersecurity Experts Can Monitor And Spot Cyber-Attacks, Including Ones That Involve Compromised Credit Card Data.
Cybersecurity experts use a variety of tools, strategies and techniques to recognize and monitor cyber-related threats, such as compromised credit card data. A few common practices and techniques are: Threat Intelligence Gathering
To keep up-to-date with threats and vulnerabilities, it is essential to gather information from various sources. These include forums and threat feeds and dark web monitoring tools, and security advisory services.
Network Monitoring & Intrusion Detection
Check the traffic on your network using specific software or tools. Detect anomalies or suspicious behaviors that could indicate unauthorized entry or data breach.
Penetration and vulnerability testsTesting for vulnerability and penetration
Conducting regular assessments in order to detect weaknesses. Penetration testing involves simulated attacks to find weaknesses and evaluate your organization's cybersecurity capabilities.
Security Information and Event Management, (SIEM),
Implementing SIEM solutions to aggregate and analyze logs gathered from different sources, like servers and firewalls, to identify and respond to security breaches immediately.
Behavioral Analytics
Utilize behavioral analysis to identify unusual patterns or changes in user behavior, within networks or in systems. This could signal the possibility of a breach.
Threat Hunting
Looking for suspicious or threats activity on the network of an organisation using logs, traffic and system information. This may help to identify dangers that aren't being detected using traditional security measures.
Endpoint Security Solutions
Utilize endpoint security (such anti-malware programs as well as endpoint detection and response tools and others.) to protect endpoints and individual devices from malicious activities.
Data Protection and encryption
To minimize the risk of data breach, implement encryption techniques for sensitive data like credit card numbers, both during transit and while at rest.
Incident Response & Forensics
Implementing incident response plans can allow you to swiftly respond to incidents. Conducting forensic analysis to identify security breaches and determine their impact and cause.
Cybersecurity specialists combine these approaches and have a thorough understanding of guidelines and best practices for compliance to identify, minimize and respond quickly to cyber threats. To maintain a strong defense against cyber-threats it is essential to keep a constantly monitored system, a threat intelligence program, and an active security strategy. See the top rated savastan0 cc dumps for website tips.
